XTRF Single Sign-On (SSO) configuration
This is an old version of the article. Please check the actual version in our new Knowledge Base.
This topic is to help the administrators configure SSO in all XTRF Portals.
SSO is optional and each XTRF Portal can be configured separately, to use traditional credentials, credentials + SSO, or SSO exclusively.
Basic SSO configuration
Check the compatibility
Once Single Sign-On is activated on the license server, it’s time to connect the selected Portal with the external Identity Provider compatible with OpenID Connect standard. Popular providers include Google, Microsoft Azure, GitHub, Paypal, Salesforce, among others.
XTRF SSO internally uses Google APIs Client Library to communicate with the provider over OAuth 2.0 protocol. Authorization flow is compatible with OpenID Connect Core specification on top of OAuth 2.0. XTRF SSO uses Authorization Code Flow from OpenID Connect specification which means you need to configure both authorization endpoint URL and token endpoint URL on the XTRF configuration page.
All top Identity Providers use protocols compatible with the one used by XTRF.
Register with the Identity Provider
To connect with the Identity Provider, you need to register XTRF as a client application on their server.
Steps:
- In the Home Portal go to
General Configuration > Security > choose Home Portal / Vendor Portal or Client Portal.
Get the Callback URL. It is the address you will be redirected to, after your application is authorized. You will need it for the registration form. - Go to the Identity Provider’s web location and fill out their registration form. Here are the steps to follow with the most popular Identity Providers:
Instructions for Google
Instructions for Microsoft Azure
Instructions for GitHub
Note:
When the registration process is complete, you will receive two unique variables which need to be noted:
- Client ID
- Client Secret
Configure XTRF
Back in Home Portal’s General Configuration > Security > choose Home Portal / Vendor Portal / Client Portal and fill out the SSO configuration form, including the variables acquired during the registration.
The basic configuration includes the following parameters:
- Auth URL - the endpoint for authorization server. It is used to obtain the authorization code (e.g. https://id.yourdomain.com/adfs/oauth2/authorize).
- Access Token URL - the endpoint for the authorization server. It is used to exchange the authorization code for an access token (e.g. https://id.yourdomain.com/adfs/oauth2/token).
- Client ID
- Client Secret
- Scopes (optional) - the scope of the access request used during advanced configuration. It may have multiple space-delimited values. Scopes are specific to other services the authentication provider grants access to.
Example (Google): openid email profile
Example (ActiveDirectory): openid
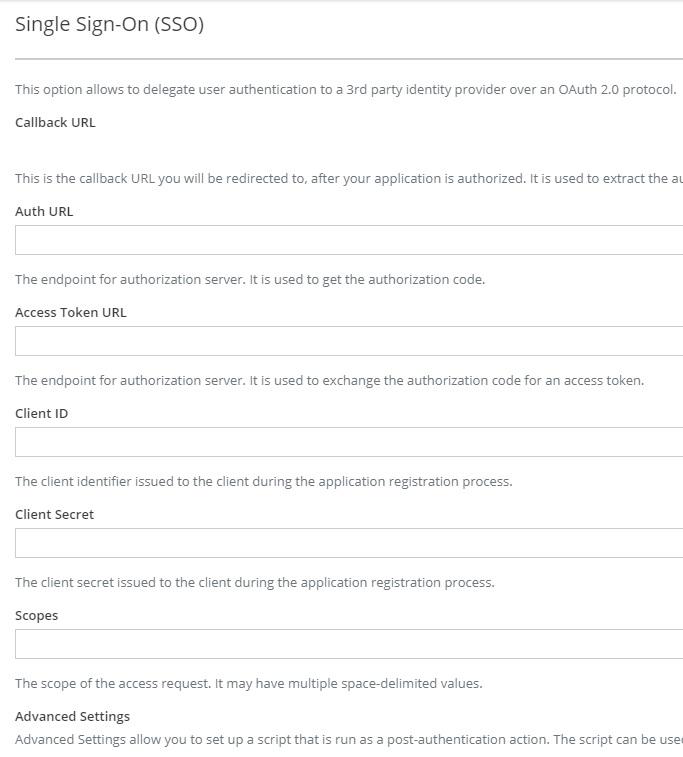
SSO configuration form in XTRF security settings
Requirements for Home Portal Users
Home Portal SSO will allow users who already exist in the XTRF System to sign in. It is crucial to remember that users will be mapped by e-mail address.
After the first sign in, the user will be matched by a key consisting of two fields: subject and issuer. Google Oauth2 documentation describes these fields as:
Claim | Provided | Description |
iss | always | The Issuer Identifier for the Issuer of the response. Always https://accounts.google.com or accounts.google.com for Google ID tokens. |
sub | always | An identifier for the user, unique among all Google accounts and never reused. A Google account can have multiple email addresses at different points in time, but the sub value is never changed. Use sub within your application as the unique-identifier key for the user. Maximum length of 255 case-sensitive ASCII characters. |
Requirements for Vendor Portal / Client Portal Users
There is no way to sign into Vendor / Client Portal with SSO by using an account set up for an enterprise. Only contact persons within the enterprise account will be recognized by SSO as system users.
Advanced SSO configuration
The general purpose of advanced configuration is to enable elements of user provisioning functionality. Advanced configuration is carried out with a Groovy script that is run as a post-authentication action. The script can be used to synchronize certain pieces of user data between the XTRF database and SSO provider, including user profile details or group assignments (and thus the user rights)
To see the most popular cases of user provisioning configuration with default pieces of code, please contact the XTRF Helpdesk.
XTRF SSO Installation and Configuration Guide
Read also:
Customer support service by UserEcho

