SSO or Single Sign-on
This is an old version of the article. Please check the actual version in our new Knowledge Base.
If you prefer your team to have all professional network destinations available via one access point, you can include XTRF in it as well.
What is a Single Sign-On?
Single sign-on (SSO) is a feature that facilitates access to multiple applications by using only one set of credentials. This is possible by relegating identity authentication to a third-party service (Identity Provider), to which other applications have relegated this requirement as well. Being authenticated by the Identity Provider allows you to sign in to those other applications without the need to re-enter your username and password.
XTRF SSO uses OpenID Connect standard for relegating authentication. Popular OpenID Connect Identity Providers are Google, Microsoft Azure, Yahoo, Salesforce, GitHub, among others. SSO can be activated and configured independently for all three XTRF portals.
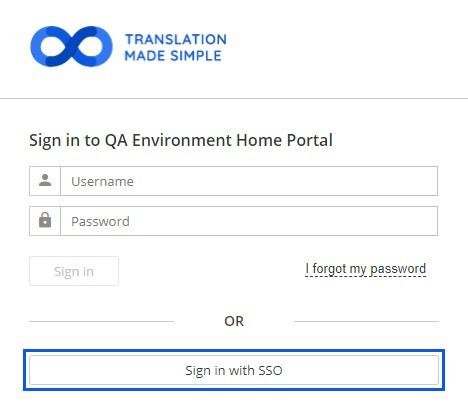
XTRF sign-in screen with both regular sign in and SSO enabled
Benefits of using SSO
The greatest advantage of SSO is that it simplifies the login process, streamlines the workflow and increases the data safety. Major benefits include:
- Easier password management. It’s safer to memorize one extra strong password instead of many.
- Better protection, reduced vulnerability. Significantly reduced risk of human error, possible two-factor authentication (2FA) and multifactor authentication (MFA).
- Better user experience. Especially when working with a large database of outside vendors. Better access speed, plus less passwords = less headache.
How does SSO work
Steps:
- The user logs into XTRF with the SSO feature.
- XTRF SSO delegates identity authentication to an Identity Provider indicated in the configuration.
- Identity Provider confirms the user’s identity.
- (Optional) XTRF SSO may run some custom post-login actions like updating XTRF user profile, user group assignments, etc.
Note
SSO is optional and each XTRF Portal can be configured separately, to use traditional credentials, credentials + SSO, or SSO exclusively.
How to activate XTRF SSO
Contact the XTRF Helpdesk for activation.
How to sign in to XTRF with SSO
- Select the Sign in with SSO button.
If you have already logged into some other platform through your Identity Provider service, you will be automatically signed into XTRF as well, and step 2 will not be necessary.
If not, you will be redirected to the sign-in page of the Identity Provider (Google, Microsoft, GitHub, or other) that the owner of the XTRF Platform selected. - Sign in with the credentials of your Google Account, Microsoft Account, Yahoo, Salesforce, GitHub, or other.
- (Optional) If the owner of your XTRF Platform requires additional authentication, you will be requested to provide it.
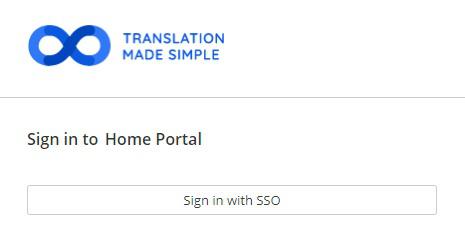
XTRF sign-in screen with only SSO enabled
SSO impact on XTRF Portals
When SSO is selected exclusively as the gateway to XTRF, certain features are disabled to maintain the integrity of the system.
Logically, password management options are gone, as XTRF passwords are not required anymore. Password-related endpoints in the APIs are also disabled. SSO also slightly changes the Vendor Portal invitation process and the range of permissions available to new users.
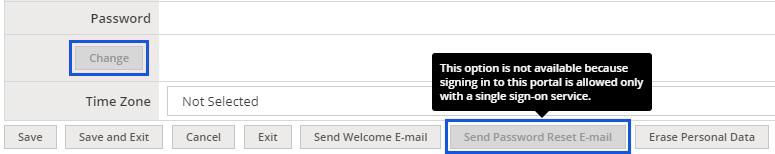
Disabled ‘Change Password’ and ‘Send Password Reset E-mail’ buttons in the user profile.
For comprehensive info on XTRF features impacted by SSO please contact XTRF Helpdesk.
Deprecated feature reminder
We kindly remind you that with the release of XTRF 9.0, and the switch to OpenID Connect based single sign-on, the header based single sign-on is deprecated. The expected removal will be not earlier than Q1 2022.
See also:
Customer support service by UserEcho

